SOC2 DAST vulnerability
scanning
Dynamic Application Security Testing (DAST) vulnerability scanning identifies security weaknesses in your web applications before they reach production. Both unauthenticated and authenticated scans are supported, allowing you to test publicly accessible pages as well as content behind login forms.
Industry Standard Scanner
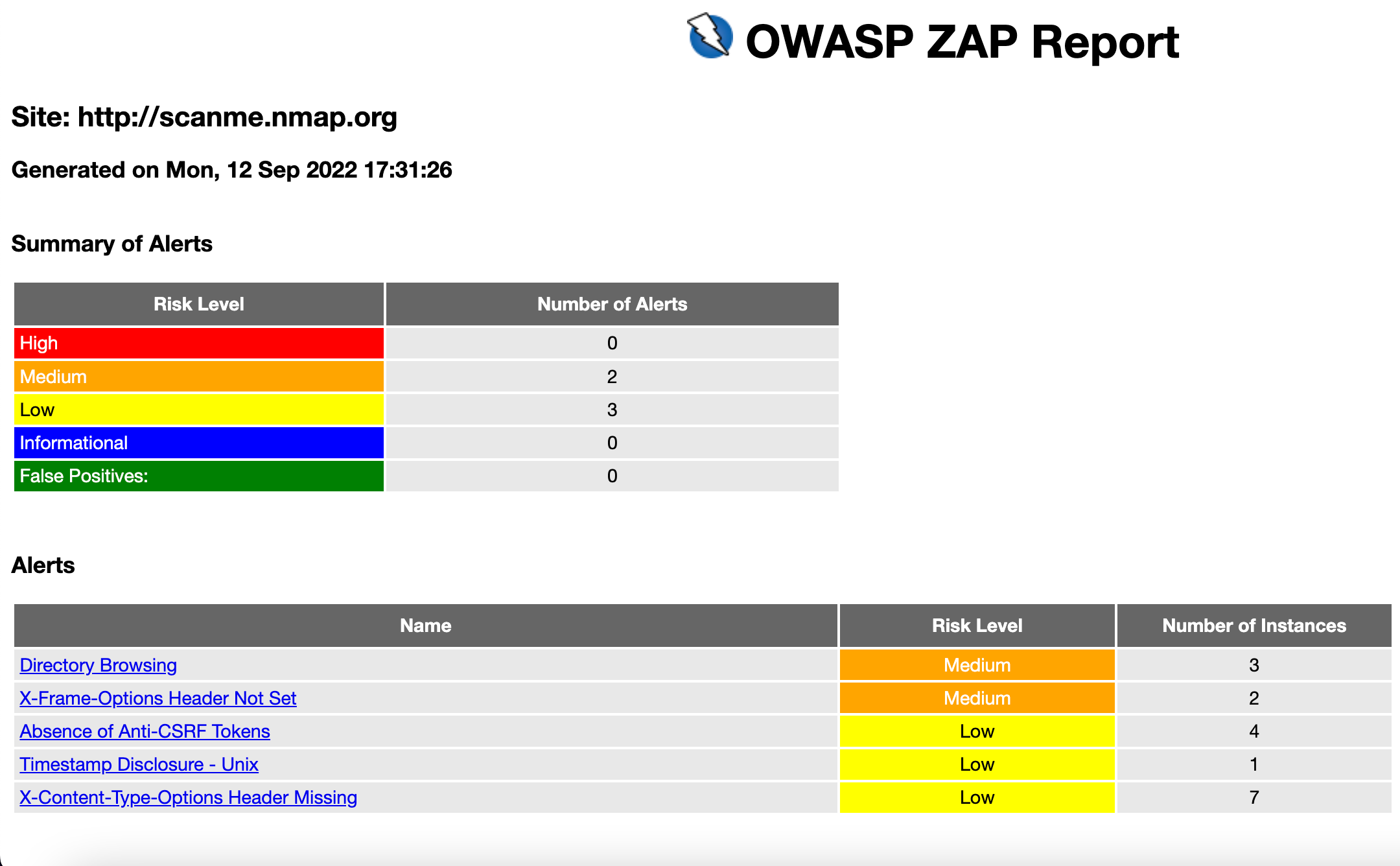
ZAP Vulnerability Scanner
Our hosted ZAP scanner provides comprehensive security testing of your web applications, identifying common vulnerabilities like SQL injection, XSS, and CSRF. Both unauthenticated and authenticated scanning modes are supported.
Seamless Integration
Built for Development Teams
Integrate security scanning into your CI/CD pipeline with our API-first approach. Automate security testing as part of your development workflow, ensuring security is built into your software development lifecycle.
Actionable Security Reports
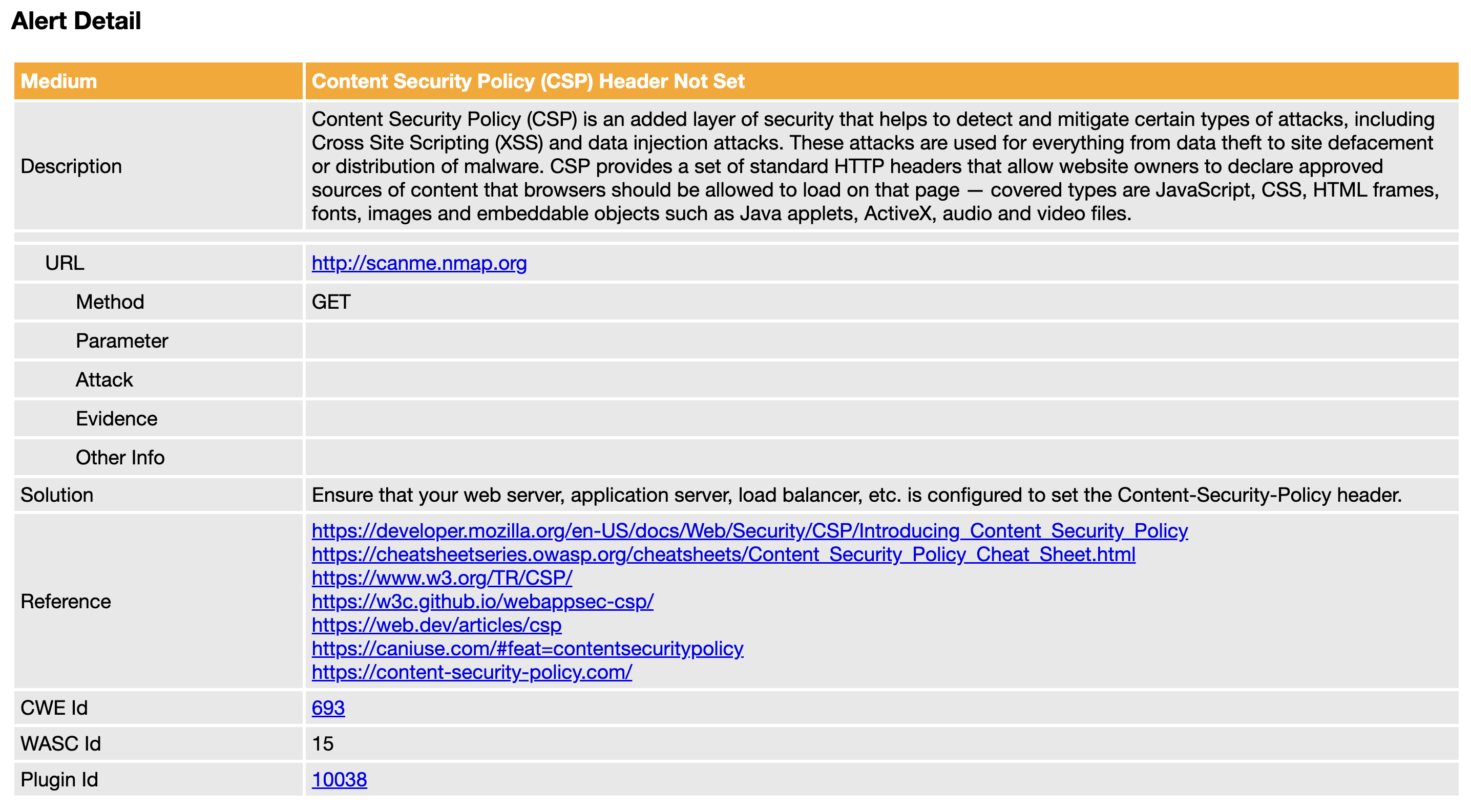
Prioritize and Fix Issues
Get detailed vulnerability reports with clear remediation steps, severity ratings, and proof-of-concept examples. Our reports help your team understand the impact and fix security issues efficiently.

Frequently Asked Questions
How many applications can I scan?
Our scanning plans are designed to scale with your needs. The free trial supports scanning of one application, while our paid plans support multiple applications with varying scan frequencies to match your development cycle.
How long do DAST scans take to complete?
DAST scan duration depends on the size and complexity of your application. Most unauthenticated scans complete within 30-60 minutes, with larger applications potentially taking a few hours. Authenticated scans may take longer as ZAP crawls pages behind login flows.
How does DAST scanning help with SOC 2 compliance?
DAST scanning helps meet several SOC 2 requirements, particularly in the Security and Availability trust service criteria. It demonstrates your commitment to identifying and addressing security vulnerabilities in your applications, which is crucial for protecting customer data and ensuring system availability. Authenticated scans provide deeper coverage by testing pages behind login forms, giving auditors confidence that your entire application has been assessed.